Wednesday, December 31, 2008
Fake AV - Stubborn to Rid from Your PC
It goes by many different names. Total Protect 2009, eXPress Antivirus 2009, iSafe 2009 (Sounds like an Apple application), Antivirus 360, Perfect Defender 2009, and on and on and on. This is just some of the more recent fake AV's that have been plaguing PC's lately.
It's tough to remove this type of malware because it defends itself very well. The best thing is to not get the nasty stuff. The most common delivery method is social engineering. Tricking you into installing the malware yourself. Be wary of messages sent to you from friends on social networking sites like MySpace, FaceBook, etc. A very effective way of propagating itself is once it is installed on a PC, any user of these social networking sites sends messages to all the friends on you list trying to trick your friends into installing this malware.
Stay safe. My Kansas University Jayhawks rocked the Insight Bowl earlier tonight 42 to 21 against Minnesota. Hope you had a safe and happy New Year!
Tuesday, December 30, 2008
More and More Fake AV!
Play it smart, don't just randomly click on things, and patch your software applications like, Adobe, all your Microsoft applications, etc. I've written previous posts that talks about the Secunia Tool that helps you keep up to date.
Stay safe, and have a Happy New Year! Rock Chalk Jayhawk. Insight Bowl on December 31.
Thursday, December 25, 2008
Same Old Story - Malicous eCards
Hopefully all of you have been good boys and girls and Santa has rewarded you well this Christmas. Take care and have a safe holiday season.
Wednesday, December 24, 2008
Antivirus 2009 Really Sucks
Well I ran across another blog today written by Gary Warner. He has a nice detailed post going into the details of how the bad guys are taking advantage of Google searches to raise their ratings that when people click on these links, it infects your PC with fake AV.
Click here to learn more on how the bad guys take advantage of things we use everyday, Google, and use it to propagate their nasty malware. Hey Nancy, this may be how it got installed on your PC!
Stay safe, have a Merry Christmas and a happy and safe New Year!
Sunday, December 21, 2008
Computer Security: Who is Responsible?
My opinion is that individual responsibility includes securing your PC at home. So when I hear a story about someone having this happen, I believe the individual really should have taken steps to secure their PC. Hey, everyone knows there are risks but who takes more responsibility? You or your bank? Well I say it is you. Owning a PC and connecting to the Internet you should know how to secure your PC for your own safety.
Computer security is so much more than just installing anti-virus and firewall. You need to know there are not so nice websites that can lead to your PC being hacked. You also need to be aware that random clicking on unsolicited links or attachments in e-mails will also get you in trouble.
Then you have organizations like the Geek Squad who really do no teaching but they are VERY willing to take your money when you mess your machine up with a bunch of crapware. You know, all that malicious software that causes your PC to run slowly and possibly be used in a botnet which really spells bad news.
So what do you do? You learn of sites that will teach you. There are a plethora of blogs and websites that talk about securing your PC. Mine and tons of others that are written by some of the brightest security people around (and I'm not including myself in that group). Take some steps to start to learn of all the threats. When I help people with their PC problems, I take that opportunity to teach them of things they should be doing to be more protected.
That is enough ranting for now. Get all that shopping done and actual save yourself some stress this Holiday season.
Thursday, December 18, 2008
Examing A Spam E-mail

Some days you get e-mails that are obviously spam e-mails. Just the little things you look at and can tell right away that it is not real. Above you can see a copy of the e-mail. Right away you know that the fake UPS e-mails are still going around. Now someone in SPAMMERVILLE should tell them UPS stands for United Parcel Service. Not United Postal Service. LOL
Have a great Thursday tomorrow!
Tuesday, December 16, 2008
Microsoft Has Early Gift for Christmas to All MS Users
Have a great Out of Band Patch Wednesday!
All Versions of Microsoft Internet Explorer Vulnerable
Have a fabulous Tuesday!
Saturday, December 13, 2008
Defend Against the Zero Day Internet Explorer Vulnerability
After downloading the browser, then you can install a great tool that works with the Firefox browser called NoScript. Just Google it and you will find it. Install that tool and play with the settings. Trust me, it will take some getting used to but after you have your web sites you visit regularly setup, then it is a piece of cake. I've written previous posts about Firefox and NoScript so look back at those if you like.
If you really want to get wild and crazy, install Ubuntu on your PC at home and test drive it. The current version is 8.10. It installs great and after you get done, you will have a dual boot option of your normal Windows operating system, but you will also have a more secure OS in Ubuntu. Live on the wild side and test drive it today. Can't think of a better time to do so.
Have a great weekend and I will try to do the same.
Wednesday, December 10, 2008
Fake AV Still Going Strong!
Patch, be careful when opening attachments, and don't just randomly click on links or attachments in unsolicited e-mails. Read the story I posted about Secunia's PSI tool to assist you in keeping your PC patched so the bad guys don't have such an easy time at your expense. Take care!
Microsoft Patch Tuesday an Early Present
Keep Updated with Secunia's PSI
In a time where you really need to stay on top of things, this little application really does a nice job. So there is no excuse now. Keep up with all those Adobe, Java, Skype, AOL Instant Messenger, and more when you are need of a patch.
It is late Wednesday the day after Patch Tuesday and Microsoft had a large present for you this December so remember if you don't have your PC set to download those updates for you, go check and get your PC patched.
Have a great Thursday and Rock Chalk Jayhawk! Go KU!!
Sunday, December 7, 2008
FaceBook Being Used to Spread Malware
This is a type of social engineering that makes you click on something and is sort of a trojan (something malicious posing as some useful application). Patching your machine is probably your best defense that you can do for yourself. One tool you can use that checks a wide variety of software on your PC is one from Secunia. Click here to scan your PC to see if you have any vulnerabilities that need patching.
Take care and have a fabulous Monday. I know I will.
Sunday, November 30, 2008
Small Credit Unions Equal Compter Security Risk
So how did this attack happen? First, the web sites were not coded securely which allowed the criminal attacker to inject this code into the online banking sites for these two credit unions. The attacker didn't actually access the credit union's customer accounts. However, if any of their customers innocently went to either credit union's website, they were re-directed to this malicious site. If not properly patched, these customers probably now have malicious code installed on their PC that could be a password stealer, keylogger, and is now a robot which means someone with bad intentions now controls your PC.
I've been told that the problem has been corrected but I have my doubts. Since I have an account at Educational Employees Credit Union, I will be watching this closely. The problem I see is that this was not reported and customers of EECU and KSCCU have spyware or malware installed on their PC and may not realize it.
Hopefully the company that is contracted to create and maintain these credit union's websites has found the actual vulnerability in their own code and closed this hole. From my experience in computer security, code developers are trained to write code quickly to add to a companies bottom line. They are not trained to code securely. I believe that this situation is so common and customers of these smaller banks and credit unions who have to contract with companies who develop and write code are putting the customers of these institutions in danger of criminal hackers stealing login credentials for their banks and credit union's accounts. I will be watching my credit union. Maybe you should too!
Saturday, September 20, 2008
How to Avoid Fake AV
- Spammed email messages (ecards) that contain malicious links
- Instant messaging applications where links are sent as messages
- Private messages in social networking sites
- As codecs for videos hosted on social networking sites
- Downloaded by malware in a prior infection
- Mass SEO poisoning involving several compromised Web sites
These attacks were starting to pop up in August, and they have continued here in September. This basically tells me the attacks are pretty successful. Beware of the social engineering that actually tricks you into installing this rogue AV badware from the criminal attackers.
Stay safe and have a great weekend.
Saturday, September 13, 2008
Fire Fighters Targeted in Phishing Scam
Click here to read the full story. Remember my advise. If it sounds too good, it probably is. And last, never respond to unsolicited e-mails. Protect yourself and your financial health. Stay safe and we are thinking of those being affected by Ike.
Sunday, September 7, 2008
Cleaner 2009 = Fake AV
Cleaner 2009 prompts users with multiple warning messages and popups that state Cleaner 2009 detected spyware on the machine. This is a poor attempt by Cleaner 2009 to get you to purchase the Cleaner 2009 program. Cleaner 2009 program may be difficult to remove manually. I've had a few machines that I have seen with the fake AV on it and it is a pesky thing to get rid of. Popular rogue anti-spyware programs like Cleaner 2009 are dressed up and renamed to confuse unsuspecting computer users.
Stay safe and have a fabulous weekend!
Thursday, September 4, 2008
Are You Getting Obama Spam Like Me?
I'm not an Obama fan. Not really that much of a McCain fan either. I do notice that I haven't got these types of e-mails from the RNC. And I find at the bottom of the e-mail, an unsubscribe link. I have always advised people to NEVER click on links in spam e-mails because you don't know what the person responsible will do with this information. Those with not so good intentions use the unsubscribe link to verify that they have a valid e-mail address and that address will be "verified" in a way that these people who market these list can sell for more.
Delete all spam e-mails that you get. Never, never, never click on any links or attachments from unsolicited e-mails.



Sunday, August 31, 2008
Scammers/Spammers will use Hurricane Gustav
When these events happen, the Internet Storm Center reports on domains that are being registered. A couple of days ago, they started seeing domains being registered relating to Gustav. Here are a few of those listed in the Internet Storm Center's latest post. Click here for the full Diary entry from the ISC.
boredatgustavus.net
contributegustav.org
contributiongustav.org
donategustav.org
donationgustav.org
gustav-hurricane.info
gustav-hurricane.net
gustav-hurricane.org
gustav-hurricane.us
gustav-relief.org
gustavassistance.org
gustavattorney.com
gustavcharities.com
gustavcharity.com
gustavclaims.net
gustavcontribution.org
gustavdonation.com
gustavfound.com
gustavhelpers.org
gustavhurricanerelief.com
gustavhurricanerelief.info
gustavhurricanerelief.net
gustavhurricanerelief.org
gustavlawsuit.com
gustavlawyer.com
gustavlegalrelief.com
gustavlegalrelief.info
gustavlouisiana.org
gustavmissing.com
gustavneworleans.com
gustavneworleans.org
gustavpictures.com
gustavrecovery.org
gustavrelief.info
gustavrelieffund.com
gustavrelieffund.org
gustavreliefvolunteers.com
gustavresponse.com
hannahrelief.org
hannainsuranceclaim.com
hannalawyer.com
hannarelief.org
helpgustavvictims.com
helpgustavvictims.net
helpgustavvictims.org
hurricanegustav08.com
hurricanegustave.info
hurricanegustavphotos.com
hurricanegustavrelief.info
hurricanegustavrelief.net
hurricanegustavrelief.org
hurricanegustavrepair.com
hurricanegustavresponse.info
hurricanegustavvictims.info
hurricanegustavvictims.org
hurricanehelp.us
hurricanelinks.info
hurricanelinks.org
hurricanerelo.com
hurricanerelo2ms.com
hurricanerelocate.com
hurricaneresponder.com
hurricaneseasonflorida.com
hurricanetrack.org
hurricanevolunteers.info
hurricanewatchnet.org
hurricanework.com
isurvivedhanna.com
lahurricanerelief.org
myhurricanephotos.com
netexashurricaneresponse.info
officialhurricanegustav2008.info
survivedgustav.com
survivedgustav.net
Some people may be registering these sites to sell in the next few days. Others may start to add "Donate Here" buttons. You need to beware of this type of scammers.
All our thoughts are with those in the Gulf Coast area. Monday is when they are scheduled to make land fall. Many have left. We all hope that this is not a repeat of Katrina. Stay safe and we'll have to see in the next 24 hours what will happen.
Tuesday, August 26, 2008
Internet Behavior Can Protect You
We've talked about this in previous entries but it is always good to review how your behavior while surfing the Internet can go a long way in protecting yourself from the bad guys. The specifics we'll talk about in this entry will be porn, P2P, and free applications on the Internet.
Porn. It is a weakness that a lot of men have and probably some women too. You have to understand that bad guys know that they want as many targets as possible so they look to what can be used to spread their evil wares. Like anyone else, bad guys want to spread their keyloggers, file stealing applications, and bot software to be able to use your computer for their evil purposes. Since many have a weakness for pornography, this is a known target for bad guys to plant their traps. My advice? Stay away. Make sure all people in your household stay away also.
P2P. Also known as peer 2 peer software. It is known as file sharing software that can be used to spread software, music, videos, and pictures. All I have to say about P2P is that you need to be warned. Not only is it illegal, you may get more that you than you bargained for. Bad guys like attaching some of their evil software along for the ride. My advice? Don't use P2P unless it is a trusted source and if it is legal.
Lastly, we'll talk free applications. I am really careful about what applications that are free that I use. I've mentioned in previous entries that I use firewall, antispyware, and antivirus that are free. When you are making the decision to download a "free" application from the Internet, it is best to actually read the EULA. The EULA is end user license agreement. You may be agreeing to be tracked so adware popups can be sent to you or your e-mail address might be given to spammers so you get even more of the e-mail crap than you do today.
Your behavior on the Internet really may be your absolutely best protection. More than antivirus, or antispyware. Be smart and don't fall for the bad guys out there trying to take advantage of you in a financial way.
That is it for now. Stay safe and have a great week!Internet Safety for Children
I've been asked, what steps should I take to protect my kids when they are on the Internet. You read on the news about predators who use the Internet to take advantage of kids. It's true. We've all seen those NBC shows where they catch predators over and over again.
The Internet gives predators an anonymity where they can build trust and intimacy very quickly. It is natural for teens to use peer support in online chat rooms to seek help with their problems. The lowest of the low pedophile know this and goes to these areas online to look for their victims. They can claim to be anyone they want to because of this anonymity that the Internet gives them.
I've heard that 1 in 5 children who use chat rooms online have been approached by pedophiles over the Internet. I've mentioned in earlier posts to avoid pornography all together for security reasons. There is one estimate that puts 20% of all Internet porn involves kids. Kids have this trust that really can put them in danger if they agree to meet someone who they met online. Adding to the nervousness of parents is that only 1 in 10 teens would ask their parents' permission to actually go meet someone who they met online.
Here is a list of key things that parents can to to protect their children.
-
The most important thing I can tell parents is have the computer that kids will use in an open setting where you can monitor their online use. NEVER ALLOW A CHILD TO HAVE A PC IN THEIR ROOM WHICH GIVES THE CHILD A SENSE OF PRIVACY.
- Talk to your kids and stress to them how to stay safe online. Have a written plan for them to read.
- Actually teach your kids how to use the Internet. Not only for your kids safety, which is most important, kids are one of the biggest computer security risks. Due to their trusting nature, they will most likely click on links that host malicious software that can be installed on your computer.
- Many ISP (Internet Service Provider like Comcast, Cox, etc.) provide parents with tools to control and monitor kids Internet use. If not, there are commercial software applications that can monitor and filter where kids can go online.
- Tell kids about the benefits of the Internet as well as the dangerous that lurk in the world wide web.
- Many kids are members of social networking sites like MySpace and Facebook. As a parent, you may want to sign up for your own account and monitor what they post on their own site. Kids tend to put TOO much information online that aides online predators in finding their victims. Also, what kids post today can haunt them later when they are looking for a job. More and more, companies do research on the Internet when deciding to hire an individual or not.
- Supervise and monitor your kids online and assist them. If problems arise, report them to the appropriate authority.
- For younger children, you find and bookmark web sites that you deem appropriate. Closely monitor younger kids.
- Have your anti-virus and anti-spware software up to date with the current signatures and run them often.
Create an online contract for teens that you can both agree to. There are many great sites online that talk about your children's safety, so definitely look at more. There are examples of contracts that I've seen that you can copy or use as a guide to create your own unique contract.
Knowledge is power. Ignorance will put you and your family in danger. Read read read. Take care out there and we'll talk again soon.
Which Browser? Internet Explorer? Firefox?
Which browser do you use when surfing the internet? Are you like most folks out there who use Microsoft Internet Explorer? The largest percentage of the population uses MSIE. I prefer to use Firefox. Firefox has gained in popularity over the past few years. Here are the reasons I use Firefox and not Internet Explorer.
Think about what the bad guy attacker thinks. If I write an exploit that takes advantage of a vulnerability, I want to hit the most largest possible target base. Simple math (I hated math by the way) and you go to the masses. I want the most targets so I write my exploit for MSIE. Simple. This is one reason why I use Firefox. I don't have that Apple mentality to think that there are no exploits written for Firefox. Trust me when I say this, there is no "safe" browser when it comes right down to it. Browsers are software and when software is written, it has bugs. So this is reason number one.
Reason number two. When bugs are discovered, Firefox has a smaller window from the time a vulnerability is discovered, to the time an update is deployed. Nothing against MSIE. I think Microsoft has come a long way from the days of old. It just seems that it takes longer for MSIE has a longer window from the time a vulnerability is discovered to the time it is patched.
Reason number three. If you are a user of MSIE, then you know with MSIE 7, you got tabbed browsing. I've been using Firefox for several years and it has had tabbed browsing for quite some time. I think there are many things that Firefox does that MSIE has moved in that same direction. Plus there are many plug ins that are awesome also. Many for security reasons.
Those are enough reasons for me to use Firefox. You ought to try it if you have never tried it. After downloading it and setting it as your default browser, browse the plug ins and see what is out there. I'll admit there are many I don't use. I have mentioned in previous posts that I do use a plug in from www.finjan.com. Be brave, try it for a couple of weeks. See if you can make yourself a smaller target out there in the wild wild west called the Internet.
If you are an Internet Explorer user, I say try Firefox and see how you like it. I believe as many in the Computer Security field do, that a change to the Firefox browser will keep you safer because you are now not wearing such a big target on your back. Take care and stay safe.
Monday, August 25, 2008
Just Say No to Debit Cards and Online Shopping
Noticed this article which emphasizes the same practice. It was in the South Bend Tribune. Click here to read the entire article.
Stay safe and have a fabulous week! Rock Chalk Jayhawk go KU!!
Thursday, August 21, 2008
Have You Run into AV2009.exe?
If you have run into this rogue Anti-virus piece of malware, click here for some removal instructions from bleepingcomputer. They also give screen shots and I have found it to be extremely helpful.
Here is a site where you too can get your geek on and read more about these fake AV malware types. Click here and here to read more.
People Really Do Click on Spam E-mails
Read this article from ZDNet and was shocked. Click here to read the blog entry from ZDNet. And NEVER click on any type of spam e-mail.
Georgia.zip Malicious Attachment
One copy of the spam was sent from an IP in Turkey. Not a place that would seem to be very friendly. So if you get this file, just trash the e-mail and don't open this file.
Stay safe and TGIF!!!
Wednesday, August 20, 2008
Protect Your Online Identity
If you think about it, if you are known in your community and you have built up a reputation, you don't want anyone to imitate your identity. A recommendation is to go out to sites like MySpace, FaceBook, LinkedIn, Twitter, and others I may not have mentioned, and sign up. You don't need to actually update the sites. Just get your name listed so nobody else can steal your online identity.
There are those with not so great intentions out there who will do this and take advantage of your reputation to possibly gain some information from unknowing people who think it's really you. So if you haven't already, go out and sign up. Protect yourself today.
Tuesday, August 19, 2008
Judge Lifts Gag Order on MIT Students - MBTA
This doesn't mean that the MBTA isn't going to try and go after these guys with criminal charges. I'm sure it will be drawn out for sure. Click here, and here for links to this story. Have a great Hump Day tomorrow!
Monday, August 18, 2008
MBTA - DefCon Talk from MIT Students
Sometimes vendors don't want you to release information. This year, there was a talk that was scheduled by three MIT students that was postponed due to a Federal court ordering them not to give the talk. The MBTA (Massachusetts Bay Transportation Authority).Those of us in attendance got to see their presentation slides that shows everything they did and what they observed.
OK, MBTA, you have a system that is broke. Hopefully you will do something about it. Come to think of it, all of the mass transit here in the US and probably abroad as well are broke too. For all of us, hopefully they will correct the problems that were discovered and will fix the broken system. Sometimes these vendors will do nothing. Kind of scary if you ask. me.
Stay safe and have a great week!
Is Anti Virus Dead?
I don't believe AV is dead. It has its purpose. There is enough malicious code floating around on the Internet for the script kiddies to get a hold of, it is a good idea to have AV. Many times when reading the Internet Storm Center's website (isc.sans.org), they will post documentation from a site I use where you can submit a file that you suspect being malicious(www.virustotal.com). It takes that file you suspect and run it against 33 anti virus engines and it documents if it is detected. Many times, only one or two actually detect it.
When trying to keep up with those really smart bad guys, AV has a more difficult time. I have always said that your behavior when browsing the Internet can either protect you or get you into trouble. Always use AV, use a firewall, and keep your signatures up to date so you will be able to detect that malicious software.
Stay safe and take care. Rock Chalk!!
Saturday, August 16, 2008
AT&T DNS Server Hacked in Texas
Well it was only a matter of time. Didn’t take too long. Seems as if Tuesday, an AT&T DNS server was compromised and anyone using that DNS server and they typed google.com, they were directed to a fake Google search page and behind the scenes there was some click fraud going on. It’s all about the money with the bad guys. You can click here to read the Techworld.com story. It isn’t too long so take a look at it.
You don’t have to think that there are more of these coming for anyone who hasn’t patched for this problem. This time was semi-harmless but you can just imagine that banking sites will start being the bait and the bad guys will gain credentials of innocent folks and they will steal money from all who are using the next compromised DNS server.
Stay safe out there folks. More of this will be coming. If you have checked out your ISP’s DNS and it is found to be vulnerable, then switch to OpenDNS.com. I wrote about that this week so take a look at it. Happy Thursday everyone!
Problem with DNS - Check Your DNS Here
On July 8th, an announcement was made public that DNS had problems. What is DNS you may ask? Well on the Internet, sites are assisned and IP Address. It is a number that would be hard to remember. For example, if you wanted to go to the web to do a search, you would have to type in 72.14.207.99. This IP is assisgned to Google. Thankfully we don’t have to remember these numbers. We can type in google.com and we can search. How can we type in google.com and be directed to 72.14.207.99? DNS. DNS directs us to the appropriate website by converting the name to an IP.
A security researcher, Dan Kaminsky, came out Tuesday saying that DNS was vulnerable to cache poisoning. This is a bad thing. If the criminal attackers can exploit DNS, they can direct you to evil IP instead of your bank.com or paypal.com and you would never know a thing. Seeing that this is a major issue, Dan gathered the folks together at Microsoft, Cisco, OpenDNS, and others. This was all kept secret until all the vendors who had issues with could patch at the same time. Doing this would correct the problem in a short time and the evil attackers could not exploit this vulnerability.
In the patches released in July from Microsoft, if you look closely at them, you’ll see a patch for DNS. Pretty important. I’ve said over and over and over. Patch, patch, patch! Now you can only do so much. Others have thing to do also. Dan has a DNS Checker to check and see if you DNS you are using has been patched. If not, you can use another DNS. Check out opendns.com to see other options you have. Opendns doesn’t have these problems.
So click on the DNS Checker link and check out your DNS today. Have a safe weekend.
Using AVG 8.0
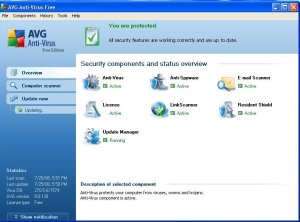
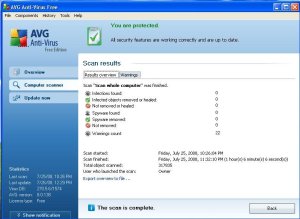
Just installing AVG 8.0 doesn’t keep your PC from needing daily attention. You should always review your daily scans. So I use AVG on my Windows XP and I have added it to friends PC’s also. I thought I would publish what steps you need to take to keep your PC running smooth. First off, you have an icon on your desktop for AVG. It is the square with 4 different colors.
After double clicking on the icon, you should see the AVG dashboard screen.
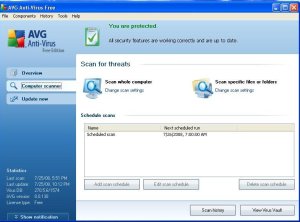
On the left, you will see 3 main tabs you can click on. Overview, Scanner, and Update Now. We will want to click on the Scanner tab to look at our scan to see if there are actions we need to take.
On this tab you will see a button on the bottome that says “View History”. We click on this button to see a list of scans that have been performed.
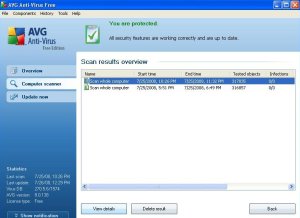
We then will select the scan we want to view and we click on the View Details button at the bottom of the screen. This will display the statistics from the scan you selected.
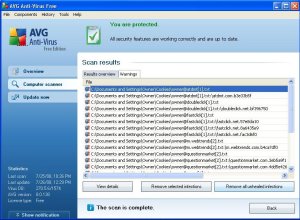
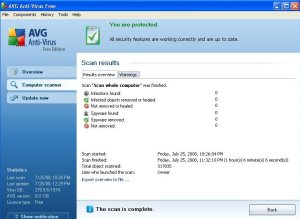
On this example, we see two tabs available to us. Results Overview and Warning. There could be a third tab if any virus’s were found. You always will want to click on the Warning tab as well as the tab that lists the virus results. In this example, I have only the Warning tab. After clicking the Warning tab, you will be presented with a list of items found. This removes all 22 of the tracking cookies that the selected scan found. Then we click on the Results Overview tab again and we see that the 22 tracking cookies have been deleted.
In this example, the Warnings tab shows us the 22 items it found in the selected scan we selected. My recommendation is to click the Remove all unhealed infections button at the bottom of this screen.
We now see 0 warnings. This deletes the warnings and if we had a Virus tab, we would do the same action. It is always a good idea to review what items were found, so this is why we go through this each day. Taking these actions will keep your PC clean as possible. If you don’t review this daily, then the files it finds will still reside on your PC each scan that is performed.
Stay safe and cool and have a great rest of the weekend!
What Would a Hacker Want with my PC?
I review SANS Internet Storm Center everyday to try and keep up with the current “bad guy” happenings that the Internet Storm Center reports back. They are a source of sharing information with the Security Community and let you know what is happening currently. The Storm Center has somewhere around 40 people who rotate 24 hour shifts and it is manned continually. The link I have in the first line of this post is the story I’m using as my source for this posting.
Have you ever asked the question, what would a hacker want with my PC? You may not bank online and you may not shop online, but you need to know what a hacker sees in your PC. Kevin Liston wrote this post to remind us that when you have a presence on the Internet, you do have things of value to the criminal mind. You have a CPU, Memory, Hard Drive, and an Internet access/IP address. From using your PC as a bot that the criminal can control, to your hard drive where they can store pirated files or even child pornography, to an IP that hasn’t been blacklisted.
If you’ve ever thought that “no hacker wants anything on my PC”, look at your PC as an asset that can be used to the hacker’s advantage to gain financially over possibly you, or others. Ignorance is your enemy. Hopefully, if you are reading this for the first time, you will come back for more knowledge.
Sometimes You Need to Reload Your PC
I wrote this post last December and thought I would update it a bit since SP 3 was released by Microsoft. So here is my updated posting on ‘Sometimes, You Need to Reload’.
Sometimes, you run across a PC that has been so mucked up that trying to clean the machine would not guarantee that all the malicious bad stuff can be removed. So you decide you have to reload your machine from scratch, then update all the software. What steps should you take before you actually delete the hard drive. Here are steps I take when I reload my PC’s. It’s not a bad thing to reload. I do it at least once a year.
Here are the steps in the order that I use and then we’ll go over them .
1. Backup your files that you want. Pictures, documents, browser shortcuts, iTunes songs, etc. Also go out to Microsoft’s website and download the SP3 service pack ISO Image. Once downloaded, burn the image to CD so after you’ve completed the step 5, you then will insert this image CD in and this will patch your XP operating system and make the updates you will go and get from Microsoft a bit quicker. Click here for the Windows XP Service Pack 3 - ISO-9660 CD Image.
2. Take an inventory of what applications you have downloaded. AOL’s Instant Messenger, Adobe Reader, etc.
3. Gather all your restore CD’s that you got when you purchased your PC.
4. Review steps 1 through 3 and double check the details of each step.
5. Start the reload process.
6. After step 5 is done, then insert your MS XP SP3 CD that you created. When the window pops up, just click Install. After this has completed, then there is the process of going out to Microsoft’s site and download all the updates.
7. Take the files that you backed up, transfer them to your PC. Keep this CD full of all your valuable data.
8. From step 2, you will need to go and download all those applications that you or your kids use.
9. This step is optional, but after backing up, and you either purchase imaging software, or use some of the freeware out there, you can take an image of your clean system before you release it to all the rest of the members of your family. This will save you many hours next time you want to do a reload. Instead of going all the way back to your original restore disks that came with your PC, you can just copy your image back to your hard drive and you can do it in less than an hour.
10. YOU ARE DONE!
Now let’s cover these in a little more detail. Backing up files means any pictures, documents, favorites from browsers, and don’t forget your iTunes songs. A good starting point is to back up your My Documents. This should get your documents that you may have created with any Microsoft Office products, and your iTunes songs. If you’ve saved pictures in the My Pictures folder, this is also included in your My Documents folder. If you have other applications and they save files such as your tax preparation programs or others like that, just make sure you are getting all your files. One easy way I save my browser Favorites this way. I use Firefox as my browser of choice. In Firefox, click on your Bookmarks>Organize Bookmarks and this will open up another window titled Bookmarks Manager. From there you just click on File>Export and then you choose the location that you want to save this back up file. I pick the Desktop so it is easy to find. Then I open up my e-mail and attach it to an e-mail I send to myself.
Next, we’ll inventory what programs we’ve downloaded and use. This includes your Adobe Reader, AOL’s AIM, Yahoo Messenger, and it may also include your firewall, spyware removal and anti-virus programs. Take a look at your Add/Remove programs to see what all is installed and that could help you not miss something. If you want to, prior to your reload, just download all those setup programs and write them to a CD. Then when you are all done reloading, you can install your firewall, anti-virus, and anti-spyware programs so you can get those installed before connecting to the Internet.
Step 3 we really don’t need to go over too much. When you bought your PC, the manufacturer also gave you restore disks so if something were to happen, you could reload your PC. Get these all gathered up and ready. We’ll even cover step 4 in this paragraph also. Double check steps 1 and 2 and make sure you are ready.
OK, step 5 is the actual reload. Just follow your manufacturers instructions. Now after that, you can run your setup programs for your firewall, anti-virus, and anti-spyware and get those installed. Then connect your PC to the Internet and download your current signature files and then you will be ready to go through the Microsoft Update process. This is Step 6. This process may need to run several times. It just depends on how long ago you bought your PC.
That leads us to Step 7. You can now take all those files you backed up and move them back to your PC’s hard drive. This step is pretty easy to do. To get those browser favorites back on your PC, just open up Firefox and go to that Bookmarks Manager where you backed them up, but instead of exporting them, you will import them. So you’ll have to go get that e-mail you sent yourself with the attached file and download it to your Desktop. Then you can import them from there. Pretty simple. It is here where I would suggest that you back those favorites up every once in awhile and e-mail them to yourself. Then you can go and get them if ever something goes wrong.
Wow, we are already on Step 8. This is where we go get all those other applications like your Adobe Reader and any other software you may have downloaded. If you did this prior to your restore, you can get all those setup programs that you downloaded and wrote to a CD. Then you have all those applications installed quickly and your machine is almost ready to go.
Now Step 9, I throw you a suggestion. From this point, your system should be about as clean as it will ever be until you reload your machine again. So if you want to save a lot of time the next time your machine, you can purchase an imaging program like Symantec’s Ghost. I don’t personally use it but it would allow you to restore from this point if sometime in the future your PC gets hosed again, you won’t have to go through all these steps.
Step 10….YOU DID IT! It really isn’t hard, but it is time consuming. This is actually a process that I go through at least once a year. Reloading your PC shouldn’t be a huge process. Anyone can do it but it takes some time. So next time you have to do this, go check out the price that the Geek Squad charges, then do it yourself and take the money you save and take your family out to dinner.
Everyone stay safe and take care.
Passwords Suck!
I tried to post this next story Monday night but was unable to beat WordPress before their maintenance. So it is now Tuesday morning. My KC Chiefs won this past Sunday. Offense didn’t look good at all. Not sure if it is me or not, but I thought the play calling wasn’t imaginative at all. But a win is a win. I still think this may be a long season. Now back to passwords sucking.
Passwords for the most part suck. Let’s admit it. If your password is a word in the dictionary, it can be cracked quickly. I give talks about computer security and when I ask when is the last time they changed a password on an email account or lets say….a PayPal account and the normal answer is they haven’t. Then when I follow up with the question, do they use a strong password? Well you can guess the answer to that one. People complain that they can’t remember a complex password. Trust me, it isn’t that hard. To truly have a strong password, you need to use upper and lower case letters, numbers, and special symbols.
Being in the business, I hear this all the time. Plus the longer you make the password the better. Here are examples of bad passwords. kujayhawks, ksuwildcats, kcchiefs, admin, password, 1234, asdf, etc.. By chance, lets say,we wanted to create a complex password. Using upper and lower case letters, numbers, and special characters you can build a password like P@s$w0rd. I would not advise you to use this but you get my point. Easy to remember. If you have an account that you really want to protect, you might look at creating a pass phrase. String out a 30 character password by using a combination of words. Substitute numbers and special characters, and use upper and lower. The longer the password, the longer it takes to crack. The shorter it is, the easier to crack.
So if you haven’t changed your P@s$w0rds in a long time, maybe you ought to think about doing just that. The longer the password, the better it will be. Remember, if some how your PC is pwned by an attacker, then there is a good chance you have a keylogger installed that will record and send off to the bad guy’s remote server somewhere in the WWW. It takes many steps to keep you safe. Not sure what we’ll talk about next posting but I have several ideas. Rememberdontu$ep@$Sw0rdsTh@tsUCk. There is a good complex password for you! You get my point I’m sure. Talk soon.
I Don’t Know What UPnP is but TURN IT OFF!
First things first. Universal Plug and Play (UPnP) is a set of computer network protocols. The goals of UPnP are to allow devices to connect seamlessly and to simplify the implementation of networks in the home and some corporate environments. This is used for data sharing, communications, and entertainment. I won’t go any further trying to explain it. To be honest, I didn’t know much about it until I started reading about the problem with UPnP. The problem is there is no authentication with UPnP. OK, that isn’t good at all. Why should you be concerned with this? Well total pwnage is what we are talking about. Some bad people can get control of your router which has horrible ramifications. If you want to more on this subject, Google UPnP and Computer Security to read additional information on this topic.
So here is what we have to do. First things first. How can we shut this off? Well you probably have purchased a router that you use in your home. One of the more popular devices is the Linksys WRT54G. Netgear sells them as well as many others. If you have never logged into your router, let me tell you how to do this. Open up Microsoft’s Internet Explorer and type in the IP address assigned to your router. Let’s say that you own a WRT54G from Linksys. Linksys routers use 192.168.1.1 for their internal IP address. Enter the address ‘http://192.168.1.1′. What you should be presented by is something like login screen that has a user name and password. If you have never changed the default password on your router, this will be a good time to do that as well as turning off UPnP. If you don’t know the default password, go here to find the default user name and password for your router. This is great router resource.
Once you have logged on successfully, you will be presented with a web interface. Normally on the left hand side of the page, you will see different areas you can check and change. If you still have the default name and password, then change this immediately. Then find where UPnP is turned on, and turn that bad boy off. Then you can click on log off, remember your password that you set and don’t set it to a word in the dictionary.
Gnucitizen (A computer security researcher) has several postings since the first of the year on UPnP. Check his blog out where he really breaks down the issues with UPnP. His point is, TURN IT OFF!
Stay safe. Rock Chalk Jayhawk GO KU!!
567,000 Private Photos From MySpace Hacked
Now I tell you this, I am no expert on MySpace. I don’t have a MySpace page. I don’t plan on getting a MySpace page. But you may have a MySpace page or your kids may have a MySpace page. And if you do, this story may have caught your attention. Not too long ago, 567,000 photos that were marked private on MySpace were accessed, copied, and now are available on a 17 gig torrent.
One of the things MySpace does to protect minors against pedophiles is to mark photos posted on their MySpace page private so only “friends” they have can access these photos. Adults who have MySpace pages also can mark photos either public or private. If they are marked private, it works the same way. Only people they have designated certain “friends” are able to access these private photos. Due to a vulnerability in the MySpace private photos, some 567,000 were extracted from the MySpace files. Now one might wonder how could MySpace not see hundreds of thousands of requests from one IP address isn’t seen. A 17 gig file is huge not to see.
Oh well. Supposedly this has been fixed. But the lesson should be this. If you ever post pictures that are supposedly private on the Internet, someday, someway, their may be a possible software vulnerability that allows someone to steal these pictures and they will live forever as a file that can be accessed. This is something I try and suggest. Never post anything that you wouldn’t mind being seen by everyone. I haven’t read any details, but I’m sure there are some nude pictures that have been posted and were assumed protected by being marked private. Well not so.
This is a good example of creating your own “need to know policy” where you don’t disclose anything about yourself online. Crooks are always looking for ways to steal information about you. If you have kids and they are on MySpace, you may want to warn them that if they had pictures marked private, there are thousands and thousands now that are public record. Some may be embarrassing, so warn them of the dangers of posting things on the Internet and don’t let people know too much about you. Protect your privacy by not disclosing anything without thoughtful consideration.
Take care and stay safe.
How to Find My SSID
So you are sitting at home, and you wonder hey, what is my SSID name? If you have a wireless access point, it has a name, and you have the option to either broadcast that name so others can see you, or not to broadcast your SSID and you can be stealth like. If you have a laptop and your have used wireless before, you know you can view networks to connect to in the Windows Operating System. The networks that show up in that window are ones that have chosen to be broadcast. There are ways to find SSID’s that aren’t broadcast (Kismet), but this article is about how you can find it.
If you purchased a wireless router and you just took it out of the box and then you plugged it in, you probably have an SSID that is the default name the company that made the AP decided to put in all their routers. For example, you can find many wireless access points with the SSID name of ‘Linksys’. Along with this, they have a default userid and password assigned to it. For security purposes, you really need to change all these names. Here is a little ‘how to’ on the administration of routers in general.
First of all, if you are guilty of just plugging in the router and not changing any of these settings, then here is what you can do. You can actually log into your router by using Microsoft’s Internet Explorer. Look up in your documentation that came with your router to know the IP address that it uses. For example, Linksys routers use 192.168.1.1 for their internal IP address. Other routers sometimes use 192.168.0.1. So in MSIE, you would enter the address ‘http://192.168.1.1′. What you should be presented by is something like login screen that has a user name and password. Here is where you either look this information up in the router documentation or Google the type of router you have for this information. Also, you can reference a site I always have handy that tells you the default router userid’s and passwords (http://routerpasswords.com). This is another reason why you want to change these. Everyone has access to these if they know where to look. Some vendors don’t allow you to change the userid, but you can change the password.
Once you have logged in, you can change these values for security purposes. If you are logging into a wireless AP, here is where you can decide to either broadcast your SSID or not. Also you can change the name also. I advise all people to change the name of the SSID and also not to broadcast it. Change the password to a strong password to help protect yourself from someone doing cyber eavesdropping on you and your private information.
Learn to protect your information. It takes just a bit of work but it is worth it.